A new joint cybersecurity advisory from the Federal Bureau of Investigation, Cyber National Mission Force, and National Security Agency exposes new activity from the Flax Typhoon threat actor.
The cyberattackers have compromised more than 260,000 Small Office/Home Office (SOHO) routers, firewalls, Network-attached Storage, and Internet of Things devices to create a botnet capable of launching Distributed Denial of Service attacks or targeted attacks aimed at U.S. networks.
Who is Flax Typhoon?
Flax Typhoon, also known as RedJuliett and Ethereal Panda, is a China-based threat actor active since at least mid-2021, according to Microsoft. The tech giant reported that Flax Typhoon has targeted Taiwan-based organizations as well as other victims in Southeast Asia, North America, and Africa for cyberespionage purposes.
According to the FBI’s joint advisory, the group stands behind a China-based company called Integrity Tech, which has ties to the Chinese government.
Flax Typhoon has used several different IP addresses from Chinese provider China Unicom Beijing Province to control and manage the botnet. The group has also leveraged these addresses to access other operational infrastructures used in computer intrusion operations aimed at U.S. entities.
Further reports show that Chinese-based threat actors have targeted businesses and governments across the globe in recent years.
SEE: Why Your Business Needs Cybersecurity Awareness Training (TechRepublic Premium)
‘Raptor Train’ botnet
Black Lotus Labs, the threat intelligence team from cybersecurity company Lumen, published a report about Flax Typhoon’s compromising of SOHO routers and other devices. They called the botnet resulting from that activity “Raptor Train” and have been tracking it for four years.
Affected devices have been compromised by a variant of the infamous Mirai malware family, making it a weapon of choice for any cybercriminal aiming to compromise IoT devices, as they could easily modify the code for their purpose.
In the variant observed by the FBI, the malware automates the compromise of various devices by exploiting known vulnerabilities. The oldest exploited vulnerabilities date back to 2015, while the most recent occurred in July 2024. Once compromised, the device sends system and network information to an attacker-controlled C2 server.
As of September 2024, more than 80 subdomains of a w8510.com domain were associated with the botnet.
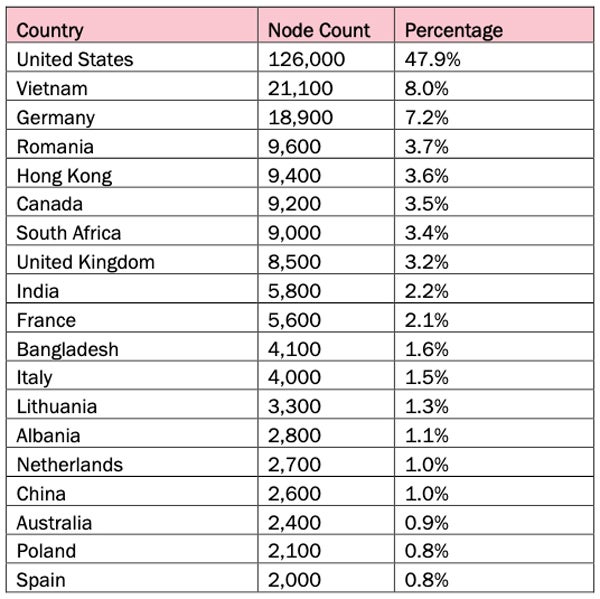
Nearly half of affected devices located in the US
In June 2024, the management servers running a front-end software called “Sparrow,” which enabled the attackers to control compromised devices, contained over 1.2 million records. This includes over 385,000 unique devices in the U.S.
A count of infected devices done in June 2024 revealed that nearly half (47.9%) of the infected devices were located in the U.S., followed by Vietnam (8%) and Germany (7.2%).
More than 50 Linux systems were compromised, ranging from unsupported, outdated versions to currently supported ones, running Linux Kernel versions from 2.6 to 5.4.
The Sparrow interface allowed the threat actor not only to list compromised devices but also to manage vulnerabilities and exploits, upload or download files, execute remote commands, and tailor IoT-based DDoS attacks at scale.
Devices compromised by the botnet cover many brands, including ASUS,TP-LINK or Zyxel routers. Also impacted were IP cameras, such as D-LINK DCS, Hikvision, Mobotix, NUUO, AXIS, and Panasonic cameras. NAS from QNAP, Synology, Fujitsu, and Zyxel were also targeted.
FBI Director Christopher Wray announced in a keynote at the 2024 Aspen Cyber Summit that a court authorization allowed the FBI to issue commands to remove the malware from the infected devices.
How businesses can protect from Flax Typhoon
The FBI recommends the following actions be taken promptly:
- Disable unused services and ports at routers and IoT devices. Services such as Universal Plug And Play or file sharing services might be abused by attackers, so all services should be disabled if not needed.
- Network segmentation must be implemented to ensure IoT devices do not pose a higher risk of compromise. The principle of least privilege must be applied so that the devices can only perform their intended function.
- Monitor for high volumes of network traffic. Organizations should prepare for abnormal traffic volumes that might be DDoS attacks.
- Deploy patches and updates for all operating systems, software, and firmware. Regular patching mitigates the exploitation of vulnerabilities.
- Replace default devices’ passwords with stronger ones so that an attacker cannot simply log in via default credentials.
The federal agency also suggested that businesses plan for device reboots — to remove fileless malware that might run in the memory — and replace end-of-life equipment with supported ones.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.


