Manufacturers in Asia are finding it more difficult than ever to manage cybersecurity demands, with challenges like zero-day vulnerabilities, increased threat sophistication and lack of investment in security keeping the industry’s cyber leaders up at night, according to digital resilience technology firm Splunk.
Splunk’s 2024 State of Security Report found 51% of global manufacturers thought cybersecurity had become harder over the last 12 months, compared with 46% across all industries (Figure A). Increases in threat sophistication were also bogging down 50% of manufacturing businesses (versus 38% overall).
This is particularly concerning for the Asia-Pacific region, which accounts for close to 50% of global manufacturing output, and includes manufacturing heavyweights China, Japan and South Korea, as well as a growing manufacturing industry in Southeast Asian nations including Vietnam and Malaysia.
Figure A
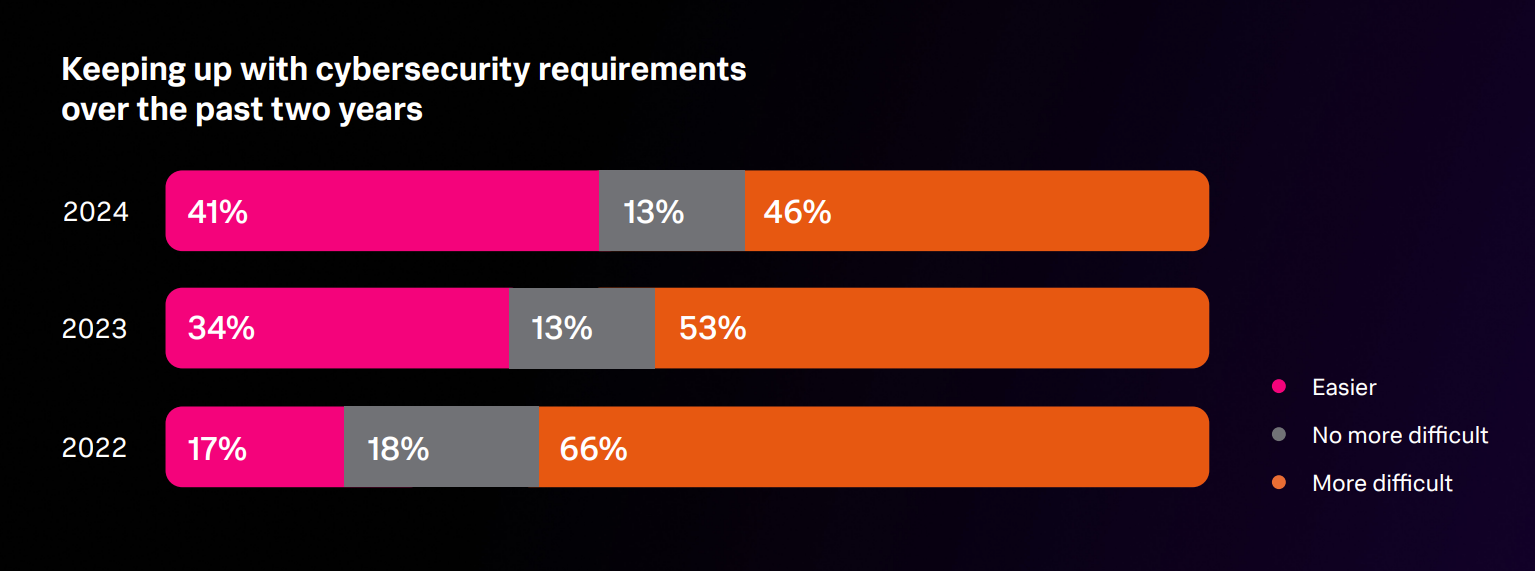
Splunk’s APAC-based Group Vice President Strategic Advisor, Robert Pizzari, said regional manufacturers were dealing with operational technology and IT environments, legacy investments in infrastructure, and extended supply chains, which can make staying on top of cybersecurity seem more difficult.
“Manufacturers typically have smaller security teams, and there is a lot of pressure on those teams. Our results show that, in an environment where they are seeing an increase in attack volumes, they are struggling to find the budget to buy or purchase the tools or resources they need to respond,” he said.
Manufacturers in Asia are facing a high volume of cyberattacks
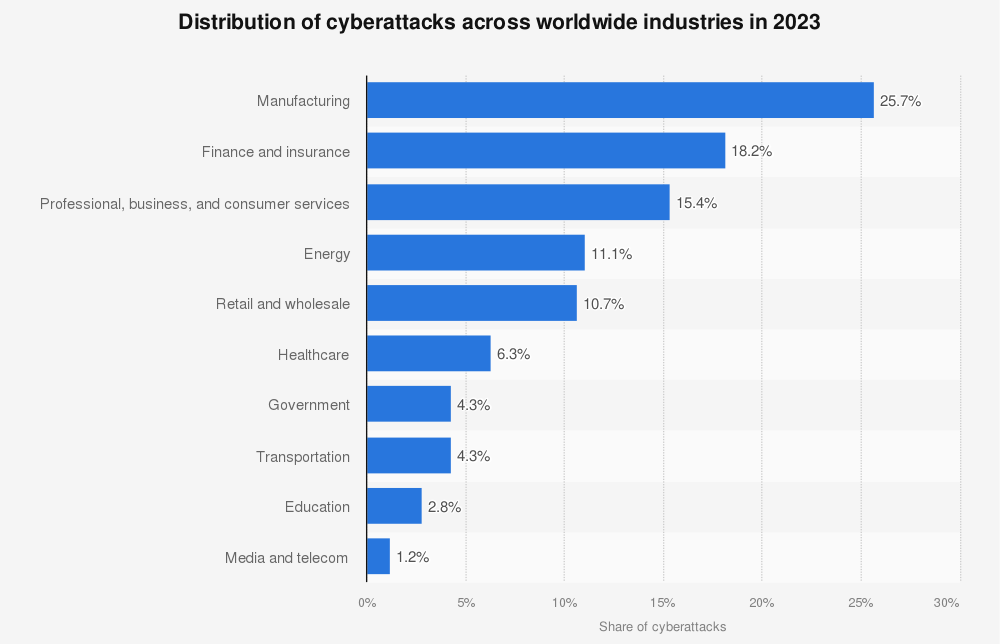
IBM’s 2024 X-Force Threat Intelligence Index found that, globally, manufacturing was the most attacked industry for three years in a row, accounting for 25.7% of all attacks (Figure B). The Asia-Pacific saw the most attacks in the global manufacturing sector, with the region accounting for 54% of all cases.
Previous research released by Splunk in 2023 also found manufacturing had become the most targeted sector by cyber criminals. Between 2019 and 2023, it found cyber attacks against supply chains had doubled, and that attacks had increased by more than 200% just during the calendar year 2022.
The manufacturing sector was also the most attacked industry in the Asia-Pacific for the second year in a row, according to IBM’s data. The top impacts named for the region were brand reputation and data theft at 27% each, while extortion, data destruction and data leaks all accounted for 20% of cases.
Figure B
According to operational technology cybersecurity provider Dragos, global manufacturing businesses also accounted for the highest percentage of incidents that were found to be ‘high severity’ by the firm in 2023, when compared with a range of other sectors that rely on utilising operational technology.
This was partially due to an increase in ransomware activity. There were 50 active ransomware groups targeting industrial organisations in 2023, an increase of 28% over the year prior, according to Dragos. Asia accounted for 119 ransomware incidents, led by attacks on the region’s manufacturing sector.
A growth in threats has not translated into cybersecurity investment. Splunk’s report found only 36% of global manufacturers expected a significant rise in security spending in the coming year, much less than the 48% of security respondents across all industries who were anticipating enhanced funding.
Manufacturers challenged by securing complex mix of technologies
Manufacturers generally have a large and dispersed supply chain, Pizzari said, making them “only as secure as their weakest link”. Often, a supply chain can include organisations without the manpower or budget to support mature cybersecurity practices, putting the end manufacturer at risk.
Manufacturing’s reliance on IoT and operational technologies is a key factor in their security posture, due to a tendency to increase vulnerabilities. A full 39% of manufacturing professionals named zero-day vulnerabilities a top concern in Splunk’s report, possibly due to the difficulty in patching infrastructure.
“Manufacturers typically have more complex networks they need to deal with and legacy investments in infrastructure. This puts manufacturers a little further behind in the race to be able to secure their environments, as well as making it just generally more complex as well,” Pizzari explained.
Dragos also found evidence of a weakness in security controls in manufacturing, where operational technology typically sits behind a firewall or proxy. Issues that involved network segmentation or improperly configured firewalls in manufacturing far outstripped other industrial sectors in 2023.
Manufacturers urged to invest more in cybersecurity
Resourcing and empowering cybersecurity is one of the four building blocks of organisations with advanced security programs. Splunk found 67% of those with advanced security programs planned to significantly increase spending over two years, compared with 28% of those with developing programs.
Splunk said security staff in manufacturing organisations should communicate the value of cybersecurity investments to stakeholders like the board, with an emphasis on the impact of cybersecurity incidents or highlighting compliance requirements with severe legal or financial consequences.
Improving cybersecurity basics can minimise risks
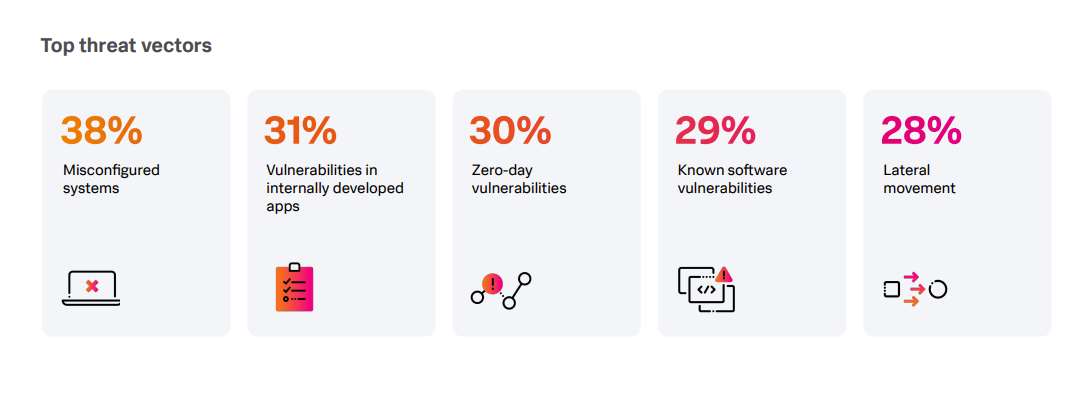
Splunk’s research found that, despite a rise in automation and the use of AI, humans are still the weakest link. Respondents across all sectors named misconfigured systems as both the most common threat vector (Figure C) and the most concerning threat vector (35%).
Pizzari said that, because there are also significant challenges that exist in the manufacturing industry from a zero-day vulnerability and patching point of view, “cyber hygiene is still really important” to the industry’s ability to combat direct threats and minimise the overall risk.
“Where they can, they should be patching. Where they can’t, they should consider how they segment or limit the potential risk of an asset being compromised,” Pizzari said.
Figure C
People plus AI could be the answer to APAC manufacturing security
Only 27% of manufacturing security professionals say that stress on the job has made them or others consider leaving cybersecurity, Splunk found, below the 36% rate across all industries, while only 27% say a critical project was delayed multiple times due to a skills gap, versus 37% across industries.
This means manufacturers are doing better at providing a reasonable place to work for security talent, though their teams are often stretched. Previous Splunk research found 56% of manufacturing security teams said they did not have enough people to handle the increasing volume of security events.
AI could add capabilities to stretched security teams
Pizzari said that Asia-Pacific manufacturers don’t have large cybersecurity teams. “The question is, how do they start to utilise other tools that are in the environment, whether it’s automation, or whether it’s AI tools, to further assist them with some of the staff shortages that they do have as well?” he asked.
“Generative AI can be great at summarising information quickly, providing guidance on next steps or detecting anomalies in your environment, from factory offices to manufacturing floors. Manufacturers who utilise generative AI could maximise the skills of the security staff they do have to improve their overall security capabilities,” he said.
The edge to enterprise dream could become a reality
Pizzari said while cyberattacks may be inevitable for manufacturers in Asia, they should not lose hope.
“Adequate cybersecurity investments and basic security hygiene can begin to reduce risk and boost resilience, ensuring security teams move from being overwhelmed to facing the future with confidence. Further mitigating factors like expanding attack surfaces or cloud security can be achieved with today’s technology – at Splunk, we are helping to make the enterprise visibility dream a reality,” he said.
With insights contributed by Harry Chichadjian, FSI & Industry Advisory Lead, APAC and Nathan Smith, Head of Security, APAC.
Access Splunk’s 2024 State of Security report.

